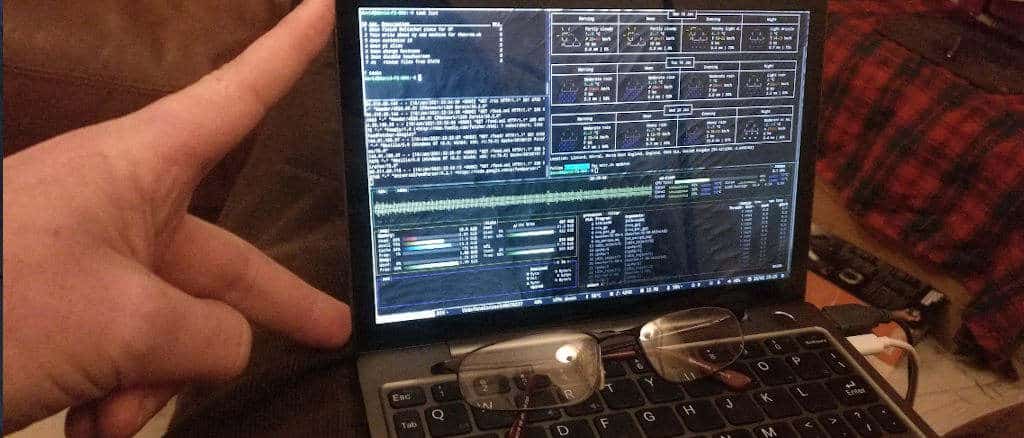
Your email is leaking - How much data you give away without ever realising.
Email is the OG of online communication, and in my opinion, it’s still pretty much the best and most efficient way of exchanging messages between two or more parties online.
For starters, the email network is federated - and that makes it, both awesome, and almost invulnerable to attack.
What am I talking about?
It’s easier to demonstrate what I mean by giving an example of what email is not, and for that I’m going to use instant messaging platforms.
Whatsapp, Facebook messenger, and signal all have similar functionality to each other. They run on their own platforms and despite the obvious similarities they are not interoperable. A Signal user cannot send a kitten pic to a user on Facebook messenger. A Whatsapp user is unable to join a group chat on Telegram. Twitter allows you to interact with other Twitter users and that’s it.
The Crow communicates by Telegram with Mrs Crow, and Mrs Crow communicates with her sister via WhatsApp. The Crow can’t communicate with Mrs Crow’s sister using instant messaging without using Mrs Crow as a bridge. That’s probably a good thing.
Email isn’t exclusive or locked in like that. Gmail users can send messages to Yahoo, Hotmail, Tutanota or anyone else. Hell, you can even buy a domain name and set up your own email server on a machine in your house. You’ll be able to use it to communicate with anyone in the world and because it’s your own, there won’t be any pesky Terms of Service limiting what you can use it for. If you’re interested a Raspberry Pi is perfect for this.
And if Hotmail or one of the other providers falls over or ceases to function, it won’t take the rest of the email network with it. If you and your buds rely on Twitter or WhatsApp for your comms, you’re at the mercy of that one provider.
But email, as awesome as it is, leaks more information than you probably realise.
What your email says about you…
The Crow is always very interested to learn more about the people who get in contact with him, and occasionally email provides a window into their lives - or at least their computer setups - than the sender probably realise.
No, I’m not talking about the username, although if an email arrives from an address containing either ‘420’ or ‘69,’ I will probably make certain assumptions about you.
The time of day an email arrives can give a clue as to the senders location - I received a mail from a generically named Tutanota account at 3.07am yesterday morning. I believe the sender is in India. I have inferred this from some idiosyncratic phrasing and the probable timezone. I could be wrong.
But one of the real gold mines in is the metadata.
What is email metadata
When you open an email, you’ll see what the sender wanted you to see. An amusing picture of a cat, perhaps. There will probably be a written message, and maybe some attached files. That’s all very nice, but most of what is sent over the email network was never meant to be seen by human eyes.
That’s not to say that it’s hidden, it’s just not prominently on display because, well, to most people it’s irrelevant and confusing.
Some of it is stuff that your email server needs to know but that you don’t really need to know unless you’re one of those strange people who is interested in how things work. Some of it is included to make sure that it displays correctly when it arrives
Open up your gmail box - go on, you probably have one. Pretty much everyone does, whether they admit it or not. Even I have one which I check into on a semi-annual basis.
If you open a message at random and click the three vertical dots, you’ll get a menu. Locate ‘Show Original’ and click on it. A new tab will open, and you’ll see a page of what looks like nonsense.
It isn’t nonsense.
What email metadata can tell you
Here’s a screenshot of some metadata from a friend of mine who works at a property management company:
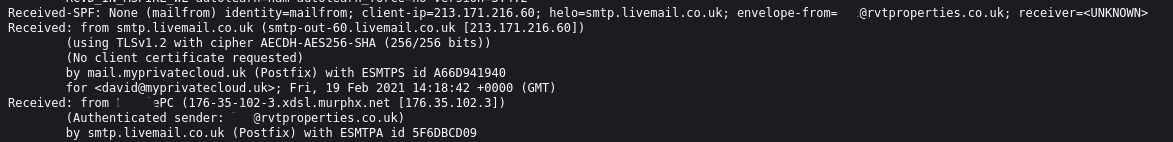
In it, along with the details of my own mail server (which I have obscured ), I can see the IP address of the office from which it was sent, along with the IP address of the mailserver.
At the time, that IP address was registered to a small business inclined service provider in the north west of England.
You can find this out by plugging it into censys.io
You will also notice that it gives the hostname of the PC which sent the message - and the username of the sender. These pieces of information, along with the IP address, make a potential target more accessible to hackers.
Scrolling down, you can see that the email was sent using Microsoft Outlook 15.0 - which is eight years old at this point, and official support stops in 2023.The version of MS Word is of the same vintage.
Does the office IT bod keep up with the latest patches from Microsoft? I have literally no idea. There’s also some information about the font settings on her system, and that she’s using a UK keyboard and spellcheck
It tells me that they don’t have SPF enabled on their email server. SPF is designed to detect forged sender addresses during the delivery of the email. This tells me that their tech bod is not on the ball.
I already knew this stuff, but then, I’m not trying to attack their system.
But you can learn more…
Using your own email server for cascade analysis.
Running your own email server makes you very aware of the pitfalls and dangers of the email system but it also gives you insight into other peoples email servers too.
Because I run my own email server and have DMARC set up correctly, for every email I send, I will get a report from the receiving server the next day giving me their verdict on my email’s trustworthiness.
It’s dull for the most part - whether or not I have enabled DKIM, SPF and DMARC; Spamassassin’s evaluation of the content that sort of thing.
It lets me know that the email has been received by the account it was sent to and didn’t land in the spam folder - which is nice. It’s not a read receipt, but it’s good enough.
This report is generated every time the email is passed on, and sends back ancillary information.
It’s not unusual for me to send an email to a client, and find out that it was received by an email server run by Zoho, forwarded to an individual who manages their email through Google, and was then shared on Slack.
That kind of information is valuable and there are all kinds of things you can learn about the relationship between individuals in a company, their relationship to each other and the information cascade between them.
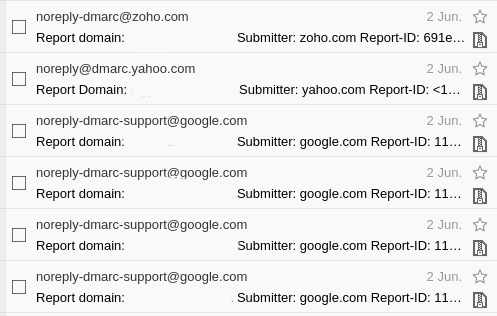
In the image above, those six reports were generated from a single email sent by me, which had been passed around other people. Inside them is a date stamp (Unix time) and server information. I can now infer who works from home, who is in charge, who makes decisions, and who gets copied in or consulted.
The bottom line
Is there a bottom line? Not really. You can be aware of these things and you can use a service like Tutanota to keep the information to a minimum. You can fake an information cascade between fictitious people with different providers to try and throw off watchers. You can create isolated email accounts and use them only to correspond with certain people and organisations. You can copy and paste text rather than forwarding emails.
Its up to you how seriously you take it.
That’s it really.
This site is hosted on a Raspberry Pi 4B in the author's living room (behind the couch). If you fancy building a website, but would prefer not to have hardware cluttering up your house, you can get reasonably priced hosting from BlueHost
On the other hand, if you're worried about being followed online, consider using PureVPN to cover your tracks.
These are affiliate links. Obviously. If you're feeling generous, you can buy me a coffee.